View our Demo Video: Please watch our short (6:33 min) NetGladiator Demo Video to learn more about our IPS technology.
See for yourself how a hacker would be thwarted by NetGladiator.
If you would like to discuss NetGladiator in more detail, please contact us.
![]()
The NetGladiator is a key device in a layered security approach. Its behavior-based anomaly detection identifies potential attackers through recognizing unusual patterns of behavior, as a hacker explores and utilizes your website much differently than a normal user. Because we can be confident in their malicious intent, we block their IP address immediately. We are not an "all-in-one solution", which can be rendered useless by alerting you thousands of times a day, can block legitimate requests, and break web functionality. We do one thing very well - we catch and stop hackers during their information gathering process - keeping your web applications secure. Information gathering is almost always the initial phase for any attack. For the attacker, it is critical to find out as much information as possible about your web server and the technologies that run on it. What is discovered in this phase is often the basis of the actual attack. Read below or download Read below or download Directory Traversal PDF Read below or download Unexpected Countries PDF SQL Injection is one of the most common and dangerous attacks web applications face today. The attack takes advantage of weakly-coded pages that interface with a back-end database. A hacker will use this weakness to run custom database queries to gather information, modify the database entries, or insert malicious code. The result can be a total compromise of your most sensitive data. Directory Traversal is one of the techniques used to discover file structure as well as software utilized by the server. This is essentially a brute force attempt to discover what files exist, what their permissions are, and what their function is in the overall web application. From almost the moment a web server has a public facing IP address, botnets from all over the world are automatically scanning it for vulnerabilities. Often, these attacks originate from countries that house very few potential users or customers for your business. Botnets can be used maliciously to perform Denial of Service (DoS) attacks, website scraping, automated downloads, etcetera. Assume you have an ecommerce store that lists products on the following URL:
http://www.mystore.com/products.php This is a clue to the attacker that a database lookup is occurring. Likely with the following query:
SELECT * FROM content WHERE id=74 Now the query to the database becomes:
SELECT * FROM content WHERE id=74 AND (SELECT 1 FROM(Select Count(*), Concat(CHAR (58,58,58), (Version()), floor(rand(0)*2), CHAR (58,58,58))x FROM Information_Schema If this is successful, the page will print out the version of mysql running on the server. This results in a proof-of-concept for the attacker, and many other, more damaging queries can be executed. Here is sample output of a directory traversal tool: You are a local business based in the United States. You sell videos to schools that teach kids how to do math. You have some online interfaces and also sell the videos online. Because the Internet is a global entity, your website is being hacked at by robots originating in China, Iran, and Morocco every day. While possible, it is very unlikely that a legitimate request for your website is coming from someone in these locations. You are putting your data at grave risk by allowing connections from IP spaces coming from unexpected countries (countries outside your normal scope of business) for the possibility of a small sale. The NetGladiator is a key device in a layered security approach. Its behavior-based anomaly detection identifies potential attackers through recognizing unusual patterns of behavior, as hackers explore and utilize your website much differently than a normal user. NetGladiator looks for database keywords in the requests destined for your web servers. The assumption is that database keywords like SELECT, FROM, and WHERE would never be in a valid URL. NetGladiator will stop this attack right away, blocking the offending IP address and alerting an administrator to the attack. Directory Traversal relies on sending many requests in a short period of time. Without the ability to send hundreds of thousands of requests, the tool used above is useless. NetGladiator stops this attack by tracking requests on a per IP basis. If the requests exceed a threshold, the IP is blocked. The assumption here is that no normal user sends thousands of requests per minute. In this case, it is best to not even allow connections from unexpected countries (countries outside your normal scope of business). This may sound harsh and somewhat sweeping at first, but good security is all about risk vs. cost. Sure, this might turn away a few potential clients, but it will keep you less visible to a large, malicious botnet. When developing an IT security policy and implementing security controls, the single most important thing to consider is how the different controls you use will layer within your security profile. Because no single piece of equipment or software will be able to thwart 100% of attacks, good layering provides the best chance to stop a hacker from their ultimate goal. To prevent SQL Injection, it’s very important to validate and sanitize the input from a form or URL before the database query is executed. This includes escaping strings, validating length, and checking the type of input to make sure it matches expected values. Diligent log review is the key to discovering locations of attacks hitting your websites. If you notice patterns in the logs indicating attacks from a specific IP range, block this IP set in NetGladiator’s user interface.
Read for yourself: To demonstrate just some of the capabilities of the NetGladiator, we have selected three (3) hacking scenarios that our product detects and prevents.

Scenario #1:
SQL Injection
SQL Injection PDF

Scenario #2:
Directory Traversal

Scenario #3:
Automated Attacks from Unexpected Countries
Description
Example
If a user wants to view a certain product, they might end up at the following URL:
http://www.mystore.com/products.php?id=74
If SQL Injection is possible, the attacker can use this knowledge to modify the above SQL query, possibly like this:
http://www.mystore.com/products.php?id=74 AND (SELECT 1 FROM(Select Count(*), Concat(CHAR (58,58,58), (Version()), floor(rand(0)*2), CHAR (58,58,58))x FROM Information_Schema>
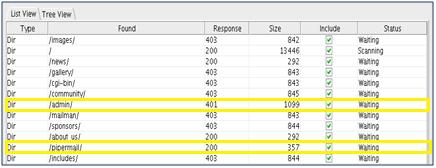
The software is brute-forcing common names from a very large list. When it gets a response code of anything other than 404 (does not exist), it prints it here for further exploration. The attacker can then manually explore interesting results (like pipermail and admin above) for vulnerabilities.
How NetGladiator Stops This Attack
NetGladiator is capable of blocking IP ranges right off the bat. IP addresses can be geo-located with relative accuracy, and NetGladiator allows you to black list these IP addresses.
Layer This With...
There are four primary actions you can take to limit the successfulness of a directory brute-forcing tool: